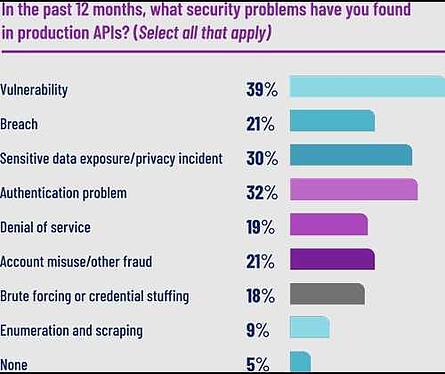
DOJ Clarifies Policy on Charging Computer Fraud and Abuse Act
On May 19, 2022, the Department of Justice (“DOJ”) announced significant clarifications to its policy on charging Computer Fraud and Abuse Act (“CFAA”) violations that give some comfort to cyber security consultants who engage in network testing and related operations. Such activity has long been a gray area for “white hat” hackers.
The CFAA, 18 U.S.C., §1030, provides the government with the authority to prosecute cyber-based crimes by making it a crime to “intentionally access[ ] a computer without authorization or exceed[ ] authorized access and thereby obtain[ ] (A) information contained in a financial record of a financial institution…(B) information from any department or agency of the United States; or, (C) information from any protected computer.” Most computers have the potential to fall under Section 1030’s definition of a “protected computer,” which includes any computer “used in or affecting interstate or foreign commerce or communication.” The new guidance demonstrates an evolving view of how the statute should be enforced with the ultimate aim of leaving the public safer as an overall result of government action. In this regard, the DOJ directive expressly states that good faith security research should not be prosecuted.
Good faith security research is defined by the DOJ as “accessing a computer solely for purposes of good-faith testing, investigation, and/or correction of a security flaw or vulnerability.” The update further clarifies that “such activity is carried out in a manner designed to avoid any harm to individuals or the public, and where the information derived from the activity is used primarily to promote the security or safety of the class of devices, machines, or online services to which the accessed computer belongs, or those who use such devices, machines, or online services.”
The updated policy further explains that, generally speaking, security research is not per se conducted in good faith. For example, research conducted for the purposes of identifying security flaws in devices and then profiting from the owners of such devices, does not constitute security research in good faith. This…