Amazon GuardDuty Enhances Security Across Industries with Advanced Malware Protection
Amazon’s GuardDuty, a comprehensive threat detection service, has significantly expanded its capabilities to offer advanced malware protection to its tens of thousands of users across various sectors worldwide. This addition is designed to strengthen defenses against a growing range of cybersecurity threats by integrating sophisticated file scanning for workloads on Amazon Elastic Block Store (Amazon EBS) volumes to identify malware presence. GuardDuty’s continuous evolution in its security approach highlights Amazon’s commitment to protecting its customers’ resources and data from unauthorized access and other cyber risks.
Robust Defense Mechanisms Against Cyber Threats
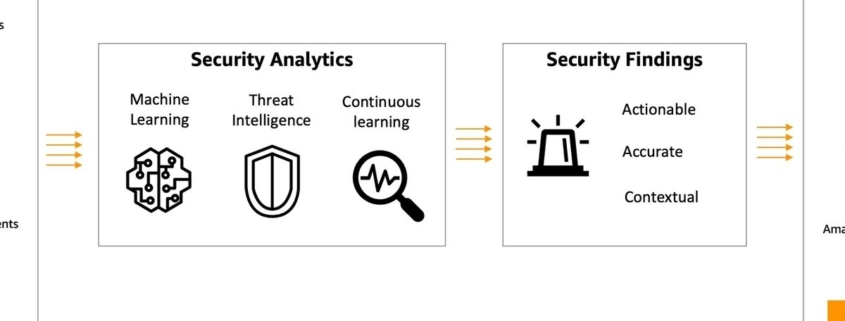
Amazon GuardDuty leverages machine learning (ML), anomaly detection, and integrated threat intelligence to identify and prioritize potential threats. This innovative approach enables GuardDuty to detect unusual or unauthorized activities, such as cryptocurrency mining, accessing Amazon Simple Storage Service (Amazon S3) data from suspicious locations, and unauthorized access to Amazon Elastic Kubernetes Service (Amazon EKS) clusters. By constantly updating its ML models and adding new anomaly detections, GuardDuty stays ahead of cybercriminals, ensuring robust security for its users.
GuardDuty Malware Protection: A Game-Changer for Cybersecurity
The introduction of GuardDuty Malware Protection marks a significant advancement in Amazon’s cybersecurity efforts. This feature extends GuardDuty’s capabilities to scan files on Amazon EBS volumes for malware, adding an extra layer of security for cloud workloads. It represents a proactive approach to cybersecurity, enabling real-time detection and response to potential threats. This development not only enhances the security posture of Amazon’s cloud environment but also offers peace of mind to the thousands of businesses relying on Amazon’s cloud services for their operations.
Implications for Businesses and Future Outlook
The continuous enhancement of Amazon GuardDuty, including the latest malware protection capabilities, underscores the importance of advanced cybersecurity measures in today’s digital…