Infowars Store Enjoyed Traffic Boost During ‘Stop the Steal”https://www.splcenter.org/hatewatch/2022/04/06/” Southern Poverty Law Center
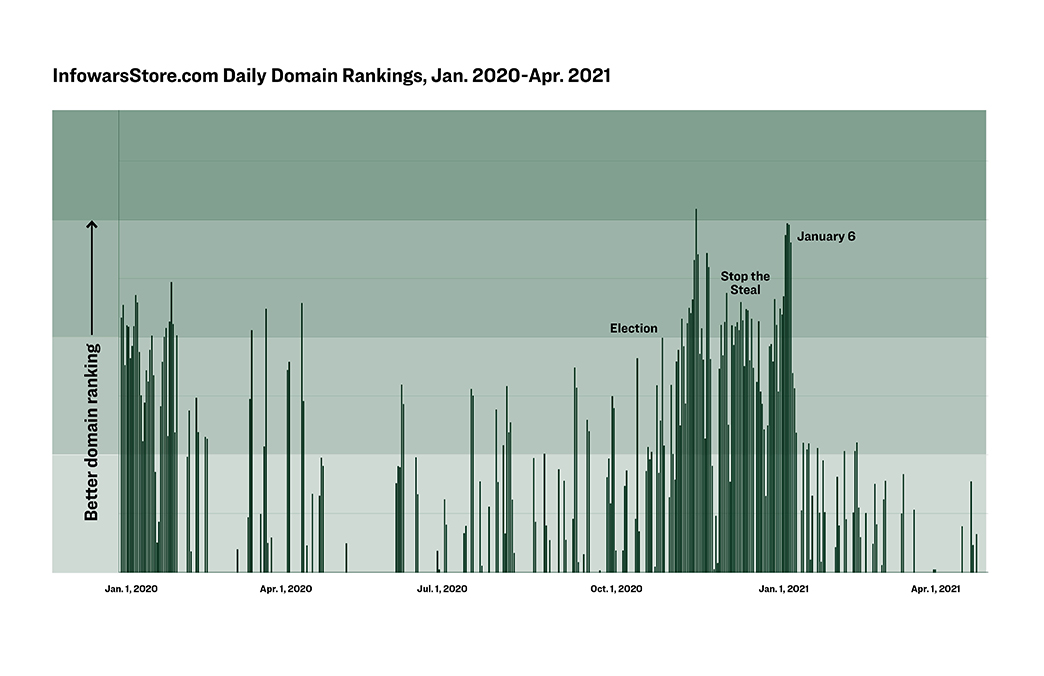
Hatewatch analyzed four years of domain ranking data on Jones’ Infowars Store from the internet security company Cisco. The data show the prolific and influential conspiracy theorist Jones faced a decline in the popularity of his store prior to Stop the Steal, but a rise during November 2020, December 2020 and the first days of January 2021. This rise in traffic hit levels the extremist had not generated since the early days of President Trump’s administration.
Hatewatch’s finding shines new light on profit-driven incentives Jones and other far-right influencers may have seen while supporting former President Trump’s election lies, as his supporters gathered to protest across the country. Jones, whose Infowars Store made $165 million in the three years from 2015-18, according to documents first obtained by HuffPost, has in private expressed revulsion over Trump.
Hatewatch previously reported on a leaked video of Jones saying in January 2019, “I’m so sick of fucking Donald Trump, man. God, I’m fucking sick of him.” Despite saying these words on camera, Jones went on to stoke anger among Trump’s supporters by perpetuating the ex-president’s inflammatory claims about election rigging that never happened. Jones promoted Trump’s Stop the Steal lies in a speech to Trump’s supporters on Jan. 5, 2021, in Washington, D.C., less than 24 hours before some of them went on to attack the Capitol.
“We have only begun to resist the globalists. We have only begun our fight against their tyranny. They have tried to steal this election in front of everyone,” Jones said on the eve of the attack on the U.S. Capitol.

Alex Jones, the founder of right-wing media group Infowars, addresses a crowd of pro-Trump protesters after they storm the grounds of the Capitol Building on Jan. 6, 2021 in Washington, D.C. A pro-Trump mob stormed the Capitol earlier, breaking windows and clashing with police officers. Trump supporters gathered in the nation’s capital today to protest the ratification of President-elect Joe Biden’s Electoral College victory over President Trump in the 2020 election. (Photo by Jon Cherry/Getty Images)
Cisco, a network security…