Hackers steal 10 million customer details from JD Sports
If you’ve purchased trainers from sports fashion retailer JD Sports in the past, your personal details could now be in the hands of hackers.
Customers of the UK high street retailer (as well as sister firms Millets, Blacks, Size?, Scotts, and Millets Sports) are being contacted with a warning that cybercriminals have accessed details of orders made between November 2018 and October 2020.
10 million people are thought to have been impacted by the security breach, which has put at risk customers’ names, addresses, email addresses, phone numbers, order details, and the final four digits of their payment cards.
An email sent by the firm to affected shoppers describes the exposed data as “limited” and underlines that full payment card details and passwords have not fallen into the hands of hackers.
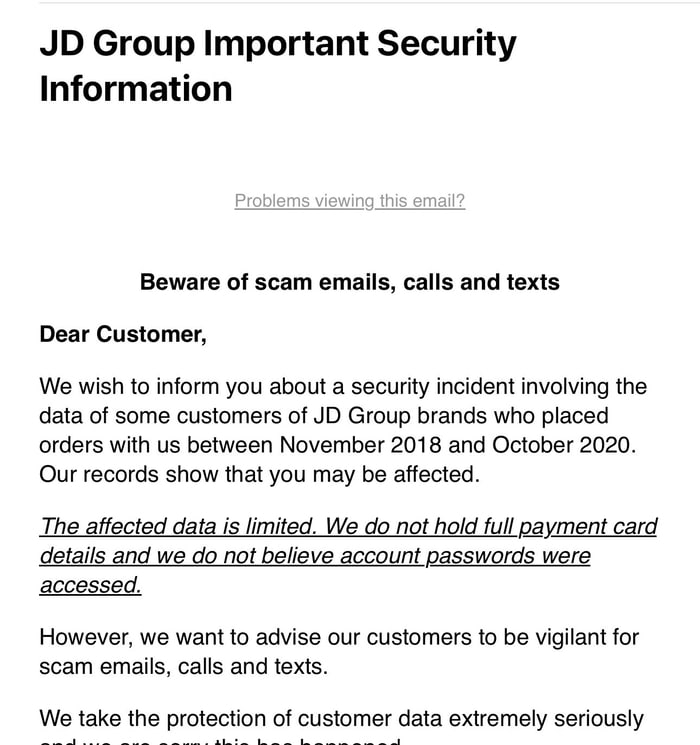
However, it is clear that the information which has been stolen by hackers is enough for JD Sports customers to be targeted with bogus communications that could attempt to steal more information from shoppers.
Accordingly, the email goes on to warn of the risk that fraudsters might exploit the exposed data to send phishing emails, or send scam calls or text messages pretending to be JD Sports or the other affected brands:
While you do not need to take any specific action, please remain vigilant to fraud attempts and be alert for any suspicious emails, calls or texts which say they are from JD Sports or any of our Group brands. Avoid clicking on links in any unexpected emails or texts.
Bizarrely, some affected customers say that the warning email they have received from JD Sports is written in Portuguese or Spanish – which would be an admirable step by JD Sports if those customers actually spoke Portuguese or Spanish, but apparently, they do not.
Neil Greenhalgh, chief financial officer of JD Sports, extended an apology to customers saying that “protecting the data of our customers is an absolute priority for JD.”
The retailer says that it has contacted the Information Commissioner’s Office (ICO) about the security breach, and is working with external experts to conduct a review of its IT security.