Product Feature | How To Detect Google/Microsoft 365 Ransomware Indicators Using ManagedMethods
When it comes to ransomware attacks, the notification that your data has been encrypted is not the beginning. It’s typically the result of days, weeks, or even months worth of effort. Monitoring for ransomware indicators means that you can detect ransomware early warning signs to stop, or at least reduce the impact of, an attack in its earliest stages.
ManagedMethods cloud security and safety platform provide a variety of monitoring and security tools to help reduce the chances of ransomware—and even phishing—attacks in your district’s Google Workspace and/or Microsoft 365 domains.
4 Ways ManagedMethods Helps District Tech Teams Identify Ransomware Indicators And Take Action
Here, we provide an overview of critical monitoring areas and best practices to help you detect ransomware indicators to avoid an attack in your district’s cloud environment. We’ll discuss how to identify indicators of attempted attacks, possible account compromisations, and concerning data oddities using ManagedMethods.
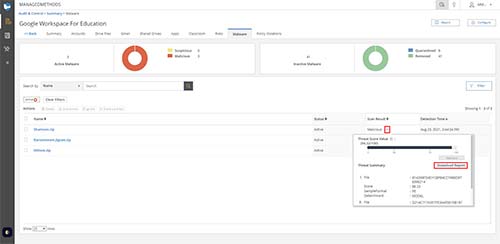 1. The Malware Tab
1. The Malware Tab
ManagedMethods partners with BlackBerry Security (formerly named Cylance) to scan for potential malware risks in your district’s Google and/or Microsoft 365 domains. This includes emails as well as drive files and shared drive files.
BlackBerry Security uses AI in combination with signature scanning, to find novel and known malware. This provides true zero-day protection for your cloud environment. BlackBerry Security also looks for malware that uses memory maliciously and allows immediate responses through policy enforcement in the ManagedMethods console.
When malware is found in your environment it will be displayed on the Malware Tab. There are two different scan results for malware:
- Malicious: Malware that is known to be malicious, or a file that is behaving maliciously. Files that are marked malicious should be treated as active malware and dealt with accordingly. It is incredibly uncommon for a file to be marked as malicious that is not.
- Suspicious: Files marked as suspicious are files that seem to be behaving maliciously, however, the AI is unable to verify the file as truly malicious. These files should be examined to see why they are…








