Don’t ignore the Apple security updates
This week, Apple warned customers of security flaws in its devices which could allow hackers to take complete control of a person’s devices. Experts say this exploitation is something to take seriously.
“This is not just kind of a run-of-the-mill bug that maybe you’re hoping your malware program is going to screen out,” Scott Shackelford, Executive Director at IU’s Center for Applied Cybersecurity Research, said.
Apple acknowledged hackers could get into phones and computers and take complete control which is why immediately patching the device is so important.
No one knows when the vulnerabilities were exploited, and Apple has not released how or by whom the issues were discovered.
“There are types of vulnerabilities that nobody knows about until they are actually released,” Mark Ostrowski, Head of Engineering at Check Point, said. “Those are the dangerous ones that you want to be sure you patch right away.”
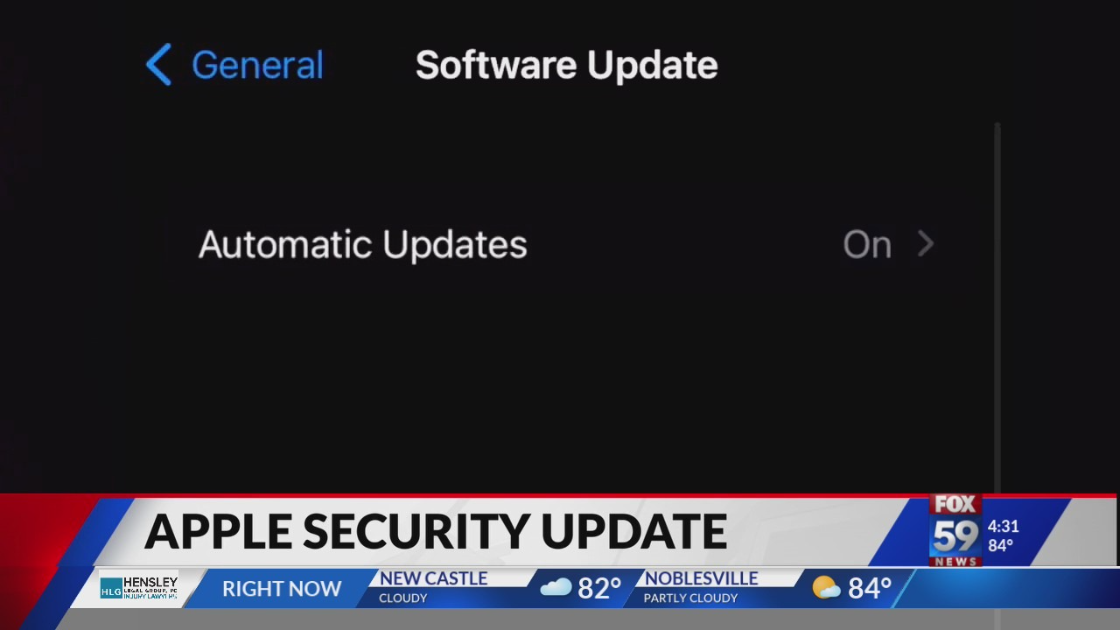
Cybersecurity experts say it’s important people have turned the automatic patches on within the phone or computer’s settings.
“The issue is, not everybody has those automatic patches turned on or we keep clicking remind me later and as a result, these systems remain vulnerable, usually for some time,” Shackelford said.
Ostrowski said this recent security flaw does not automatically victimize a user.
“You would still have to fall victim to a phishing attack where you’re providing information or going somewhere that someone is luring you to, or I would have had to have gone to a malicious website for this vulnerability to actually take action,” Ostrowski said.
Apple said those with iPhone 6s and later and many iPad models should all immediately patch their devices. Experts advise everyone to keep an eye on their accounts.