pCloud launches two free online tools to enhance security among Internet users quickly and effectively
ZUG, SWITZERLAND – Media OutReach – 2 May 2023 – In Taiwan, the need to improve online security is urgent, with organizations experiencing an average of 3,118 attacks per week last year (https://www.taiwannews.com.tw/en/news/4783488). This trend will likely worsen due to the rise in remote work and digital transformation acceleration.
It is in this context that World Password Day will take place on May 4th. One of its objectives will be to raise awareness among Internet users of best practices for securing their data.
On this occasion, pCloud, the European service that offers a secure online storage solution and an encrypted password manager, launches two free online tools:
Password Checker, to easily validate the security level of each password ;
Data Breach Checker, to find out if an email is part of a hack… and it often is!
“With data breaches on the rise in 2023, we offer these free and easy-to-use tools to help build good practices that increase online security.”
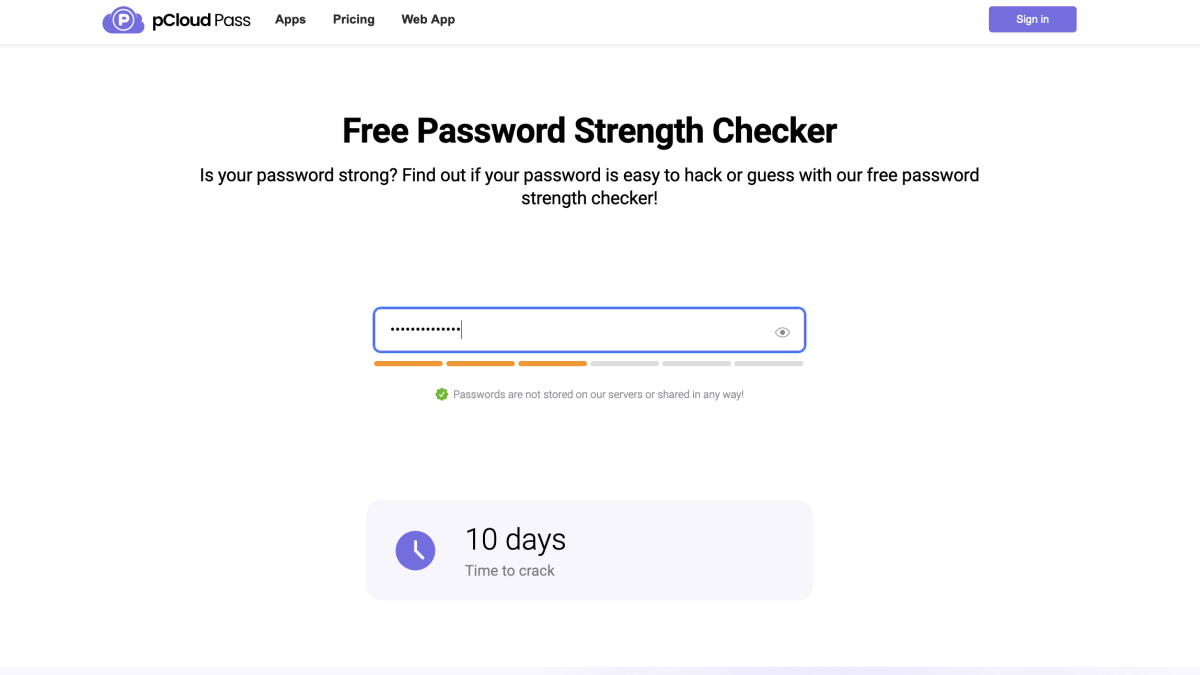
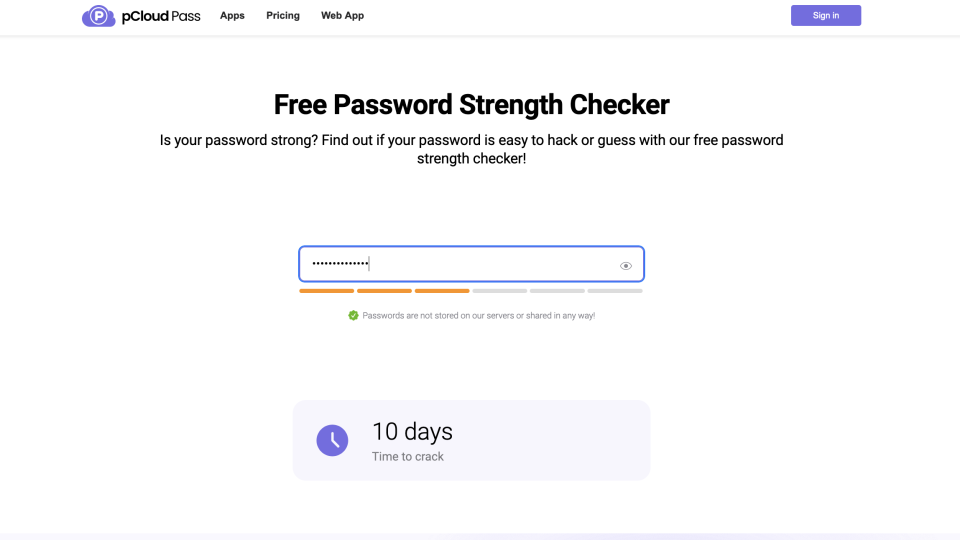
Check your password security quickly and effectively
The Password Strength Checker can identify how quickly a password can be cracked, with hackers usually taking just a few seconds to do so.
This is a significant concern since 78% of Generation Z use the same password for everything.
Concrete tips on creating strong passwords and avoiding the risk of being hacked are also shared by pCloud.
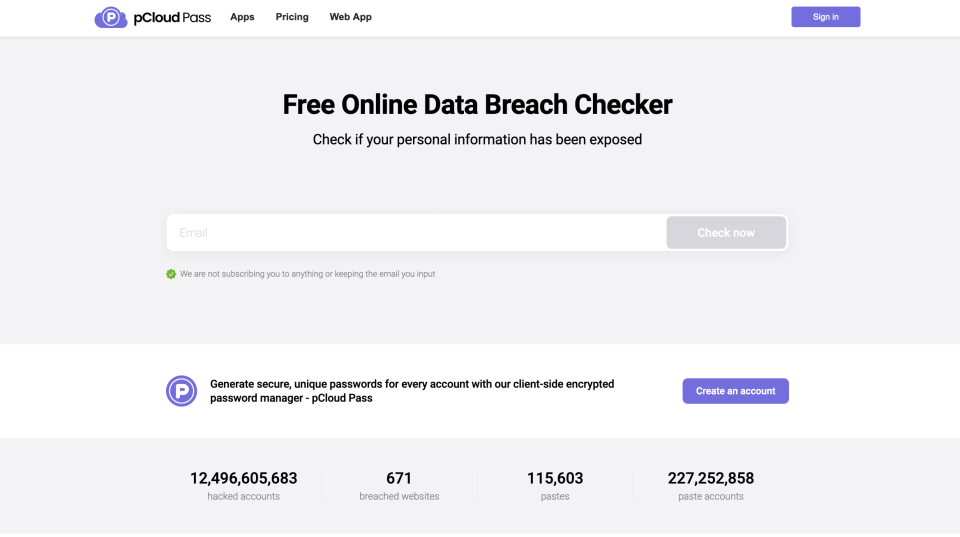
Find out immediately if an email is part of a data breach
pCloud’s Data Breach Checker allows users to find out instantly if their email is part of one or more known data breaches.
This is important since popular sites like Deezer, Twitter, Dropbox, and Canva have already been victims of data breaches.
Sensitive personal information associated with emails, such as credit cards, addresses, and passwords, may also have been hacked.
The problem is that people are not always aware of it, because they were not alerted when it happened or because they do not have a full picture of the scale of the phenomenon.
Accessible at any time, this tool allows the user to know instantly if their email is part of one or more known data breaches.
Here again, the Swiss company takes the opportunity to share 3 practical tips to ensure better…