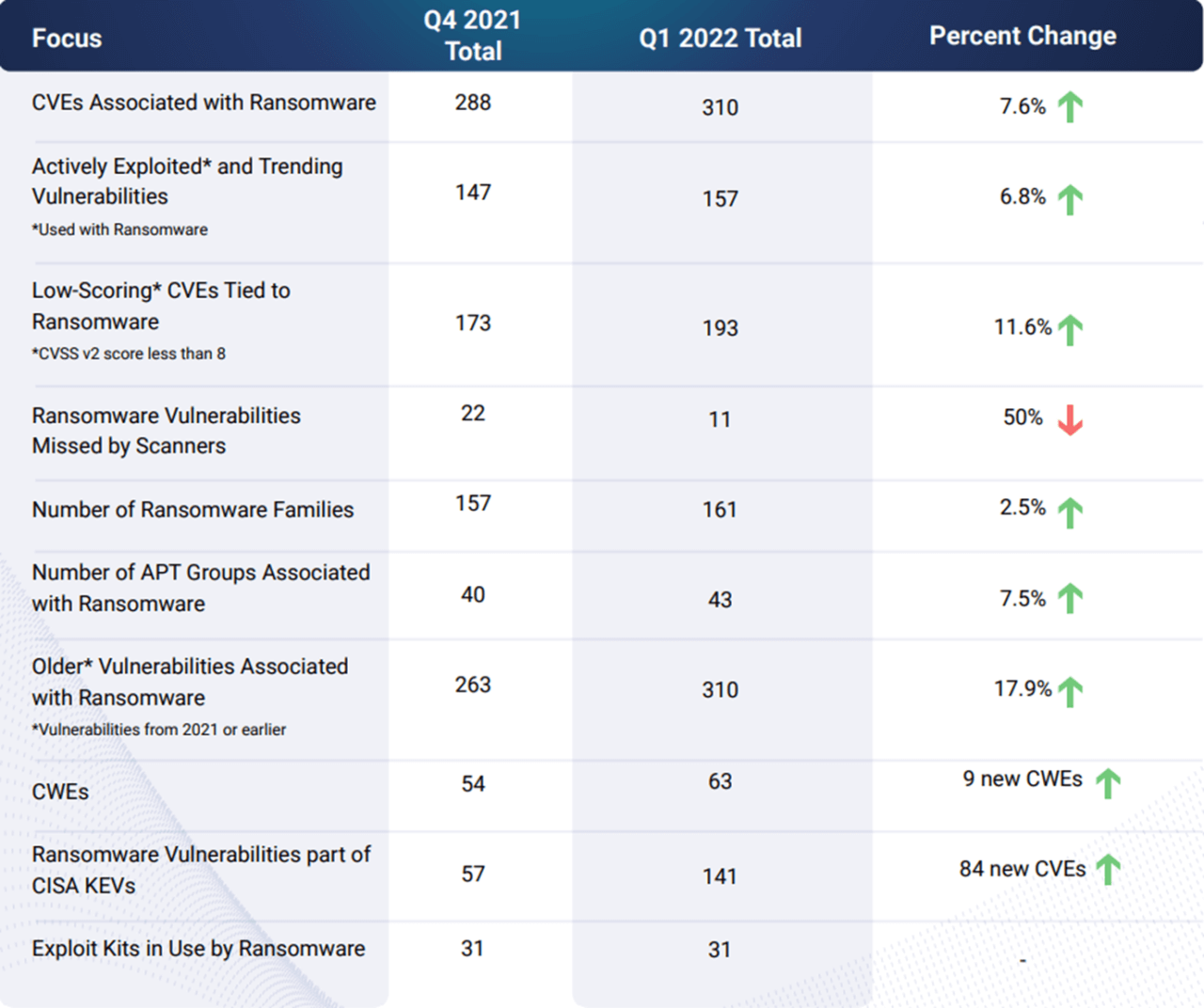
The cyberattack with the most negative impact to patient care: ransomware

A study released by Proofpoint in tandem with the Ponemon Institute found that ransomware attacks are the most likely kind of cyberattack to have a negative impact on patient care.
The report, released Thursday, said a ransomware attack could lead to procedure or test delays in 64% of the organizations surveyed and longer patient stays for 59%.
Overall, 89% of the surveyed organizations experienced an average of 43 attacks in the past 12 months, almost one attack per week. More than 20% suffering the four most common types of attacks — cloud compromise, ransomware, supply chain, and business email compromise — experienced increased patient mortality rates.
“The attacks we analyzed put a significant strain on healthcare organizations’ resources,” said Larry Ponemon, founder and chairman of the Ponemon Institute. “Their result is not only tremendous cost but also a direct impact on patient care, endangering people’s safety and well being.”
Dave Gerry, chief operating officer at Bugcrowd, said healthcare continues to be a target of attacks given its enormous attack surface across critical applications, cloud environments, and IoT devices. Gerry said ensuring critical applications, devices and systems are secure should remain the top priority for healthcare security teams.
“Bad actors understand the critical nature of the systems supporting healthcare organizations, and the human impact behind it, leading to an increased likelihood of ransom payments,” Gerry said.
John Gunn, chief executive officer of Token, said poor patient outcomes including potential deaths that result from ransomware attacks will create a liability doomsday for hospitals. Gunn said plaintiff’s lawyers will blame any negative patient outcome that occurs during a cyberattack on the security incident and the hospital’s negligence in not preventing every possible hacking attack.
“Hospitals that are unable to demonstrate the highest levels of cybersecurity will be exposed to lawsuits and judgements that could easily…