The Importance of Cyber Protection in Supply Chain | Technology
, a global leader in , today released its 2020 Acronis Cyberthreats Report, its in-depth review of the current threat landscape and projections for the coming year. Based on the protection and security challenges that were amplified by the shift to remote work during the COVID-19 pandemic, Acronis warns 2021 will bring aggressive cybercrime activity as criminals pivot their attacks from data encryption to data exfiltration.
Ransomware continues to be the leading threat, with Maze ransomware accounting for nearly half of all known cases in 2020. Yet the Acronis Cyberthreats Report points to a growing trend of cybercriminals trying to maximise their financial gain. Not content to collect ransoms to decrypt infected data, they steal proprietary – and sometimes embarrassing – data before encrypting it. They then threaten to publicly release the stolen files if the victim doesn’t pay up.
Acronis reports that more than 1,000 companies had their data leaked following a ransomware attack in 2020 – a trend that is expected to accelerate in the coming year, overtaking encryption as the criminals’ primary tactic.

“More than any year in recent memory, 2020 posed a tremendous number of challenges to IT professionals, organisations, and the service providers who support them,” noted Stas Protassov, Acronis co-founder and Technology President. “What we’ve seen is how quickly bad actors are adjusting their attacks to the new IT landscape. By analysing the activity, attacks, and trends we’ve detected and clearly presenting our findings, we hope to empower our partners and help the IT community at large prepare for the threats on the horizon.”
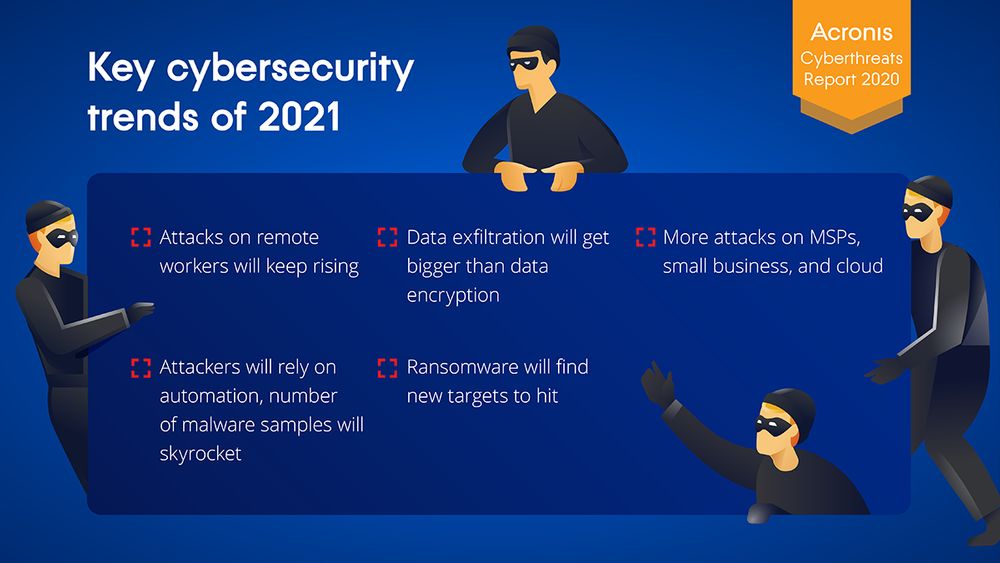
Takeaways of the Acronis Cyberthreats Report
Among the other notable findings in the Acronis Cyberthreats Report include:
- Attacks against remote workers will increase. While 31% of global companies reported daily cyberattacks in 2020, the frequency of attacks targeting their remote workers is projected to increase in 2021, since the defences for systems outside of the corporate network are more easily compromised, giving bad actors access to that organisation’s data.
- Ransomware will look for new victims, become more automated.…

