Tag Archive for: Mac’
The one security step you can’t afford to skip on your Windows or Mac
/in Computer Security
Cybercriminals are always looking for ways to get your money and info, and your phone has one vulnerability you probably never considered. Stop making this simple and dangerous mistake.
Even your printer could serve as a way in for hackers. Here are the security steps you probably didn’t know you should take.
Step away from your computer creates an opportunity for hackers, crooks, or simply nosy people with nothing better to do than snoop. Here’s how to prevent them from getting a look at what you’re doing.
Get the free 5-minute daily tech newsletter that 400,000+ people read every day.
Protect your Windows PC
You probably lock your phone when you put it in your pocket without thinking about it, but what about your computer? The same principle applies — always lock your device.

Windows computer (Cyberguy.com)
5 BEST HEADPHONES TO BOOST YOUR LISTENING FOR 2023
Even if you trust the people around you, it doesn’t take more than a passing glance for someone to cause some serious damage. That’s especially true if you work from home and have sensitive business info on your computer.
Here are some ways to lock your Windows PC:
- Hit Windows + L to lock your computer in just one step.
- Press Ctrl + Alt + Del, then select the Lock option.
- Click the Start button, then select your user icon and hit Lock.
TECH HACK: Sending and receiving texts on your computer is a total time saver. Here’s how to set it up.
Make it easier on yourself and set your computer to lock automatically after a set amount of inactivity. On a Windows machine:
- Open Settings and go to Personalization, then select Lock Screen.
- Click Screen saver settings and select any option (except None) from the Screen saver dropdown menu.
- Set a time for Windows to wait before locking. A few minutes should be fine.
- Check the box for On resume, display logon screen then hit OK.
You can also set your PC to lock automatically when you step away from it. Windows uses devices paired with your PC via Bluetooth to help detect when you’re away. Pretty neat.
First, you need to pair your device. Your phone is a good choice since you will likely take it when you get up. Find instructions for pairing any device to Windows 10 here and Windows 11…
Simple way to protect your privacy on a PC or Mac
/in Computer Security
Cybercriminals are always looking for ways to get your money and info, and your phone has one vulnerability you probably never considered. Stop making this simple and dangerous mistake.
Even your printer could serve as a way in for hackers. Here are the security steps you probably didn’t know you should take.
Stepping away from your computer creates an opportunity for hackers, crooks, or simply nosy people with nothing better to do than snoop. Here’s how to prevent them from getting a look at what you’re doing.
Get the free 5-minute daily tech newsletter that 400,000+ people read every day.
Protect your Windows PC
You probably lock your phone when you put it in your pocket without thinking about it, but what about your computer? The same principle applies — always lock your device.
Even if you trust the people around you, it doesn’t take more than a passing glance for someone to cause some serious damage. That’s especially true if you work from home and have sensitive business info on your computer.
Here are some ways to lock your Windows PC:
- Hit Windows + L to lock your computer in just one step.
- Press Ctrl + Alt + Del, then select the Lock option.
- Click the Start button, then select your user icon and hit Lock.
TECH HACK: Sending and receiving texts on your computer is a total time saver. Here’s how to set it up.
Make it easier on yourself and set your computer to lock automatically after a set amount of inactivity. On a Windows machine:
- Open Settings and go to Personalization, then select Lock Screen.
- Click Screen saver settings and select any option (except None) from the Screen saver dropdown menu.
- Set a time for Windows to wait before locking. A few minutes should be fine.
- Check the box for On resume, display logon screen, then hit OK.
You can also set your PC to lock automatically when you step away from it. Windows uses devices paired with your PC via Bluetooth to help detect when you’re away. Pretty neat.
First, you need to pair your device. Your phone is a good choice since you will likely take it when you get up. Find instructions for pairing any device to Windows 10 here and Windows 11 here.
With your phone paired to your computer, here’s how to set your…
Hacker Circulates Mac Malware Via Pirated Software Torrents
/in Computer Security
Security researchers have uncovered a largely undetected Mac-based malware that’s been circulating through pirated software downloads.
The findings come from security provider Jamf, which discovered the malware on a bootleg version of Apple’s Final Cut Pro video-editing software, which normally costs $299.99.
Jamf first spotted the malware secretly mining cryptocurrency on a customer’s Mac computer. “This particular sample was not detected as malicious by any security vendors on VirusTotal. Since January 2023, a handful of vendors have detected the malware,” it said.
Since the malware arrived through an unauthorized and modified version of Final Cut Pro, Jamf turned to The Pirate Bay, a website notorious for offering bootleg software through torrents.
“We downloaded the most recent torrent (for Final Cut Pro) with the highest number of seeders and checked the hash of the application executable. It matched the hash of the infected Final Cut Pro we had discovered in the wild. We now had our answer,” the security researchers said.
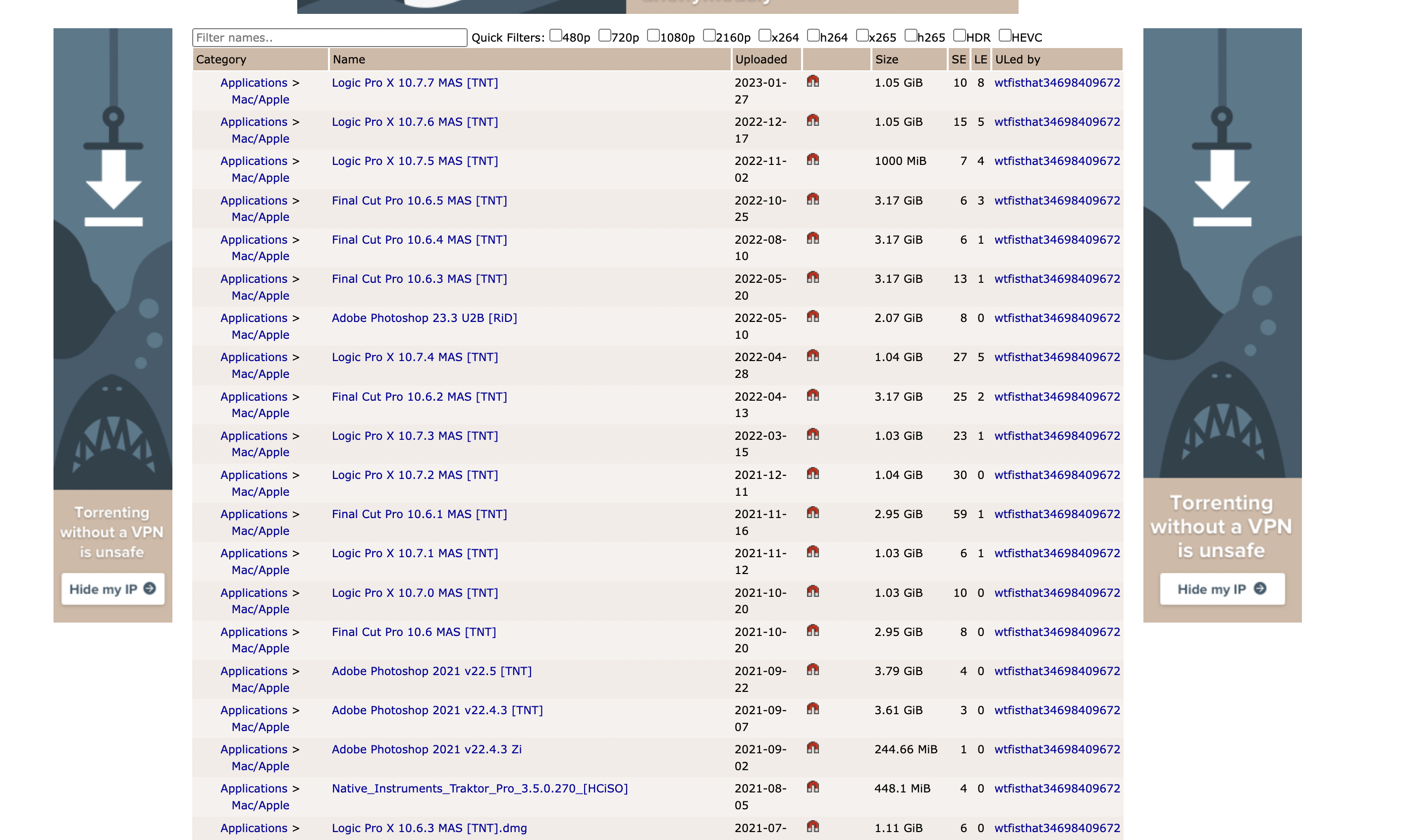
According to Jamf, an uploader on The Pirate Bay named “wtfisthat34698409672”—who has a years-long history of posting bootleg Mac software—is responsible for not only circulating the malware, but also pushing other variants of the malicious code. This includes posting malware-laden versions of Logic Pro and Photoshop.
“Furthermore, we found that virtually every one of the dozens of uploads that began in 2019 was compromised with a malicious payload to surreptitiously mine cryptocurrency,” Jamf said.
The malware itself shares similarities with another sample that antivirus provider Trend Micro discovered a year ago. At the time, Trend Micro wasn’t able to uncover the exact source, but it did speculate the infection came from an Adobe Photoshop CC installation.
Jamf says the malware has been evolving since 2019, when the hacker initially began uploading the pirated but malicious Mac software. Interestingly, the malware contains a feature that’ll check whether the user has accessed the Mac’s Activity Monitor app, which can show CPU usage.
“If it finds the Activity Monitor, it immediately terminates all of its…



