Chinese Hacking Group Exploits Barracuda Zero-Day to Target Government, Military, and Telecom
A suspected Chinese-nexus hacking group exploited a recently disclosed zero-day flaw in Barracuda Networks Email Security Gateway (ESG) appliances to breach government, military, defense and aerospace, high-tech industry, and telecom sectors as part of a global espionage campaign.
Mandiant, which is tracking the activity under the name UNC4841, described the threat actor as “highly responsive to defensive efforts” and capable of actively tweaking their modus operandi to maintain persistent access to targets.
“UNC4841 deployed new and novel malware designed to maintain presence at a small subset of high priority targets that it compromised either before the patch was released, or shortly following Barracuda’s remediation guidance,” the Google-owned threat intelligence firm said in a new technical report published today.
Almost a third of the identified affected organizations are government agencies. Interestingly enough, some of the earliest compromises appear to have taken place on a small number of devices geolocated to mainland China.
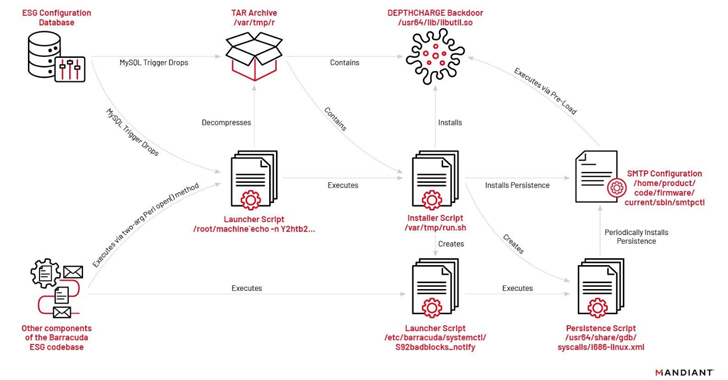
The attacks entail the exploitation of CVE-2023-2868 to deploy malware and conduct post-exploitation activities. In select cases, the intrusions have led to the deployment of additional malware, such as SUBMARINE (aka DEPTHCHARGE), to maintain persistence in response to remediation endeavors.
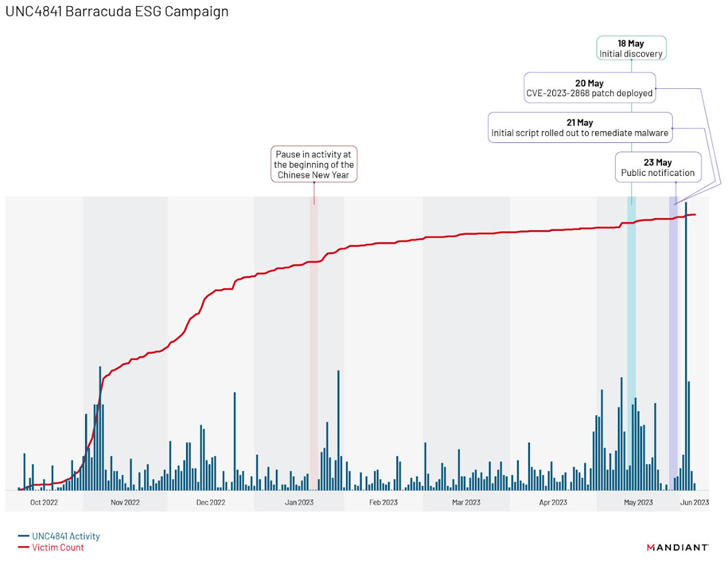
Further analysis of the campaign has revealed a “distinct fall off in activity from approximately January 20 to January 22, 2023,” coinciding with the beginning of the Chinese New Year, followed by two surges, one after Barracuda’s public notification on May 23, 2023, and a second one in early June 2023.

The latter is said to have involved the attacker “attempting to maintain access to compromised environments via the deployment of the new malware families SKIPJACK, DEPTHCHARGE, and FOXTROT / FOXGLOVE.”
While SKIPJACK is a passive implant that registers a listener for specific incoming email headers and subjects before decoding and running their content, DEPTHCHARGE is pre-loaded into the Barracuda SMTP (BSMTP) daemon using the LD_PRELOAD environment variable, and retrieves encrypted commands for execution.
The earliest use of DEPTHCHARGE dates back to May…