Military Access, Mobility & Safety Improvement Program Updates for Week of April 30 — Colorado Department of Transportation
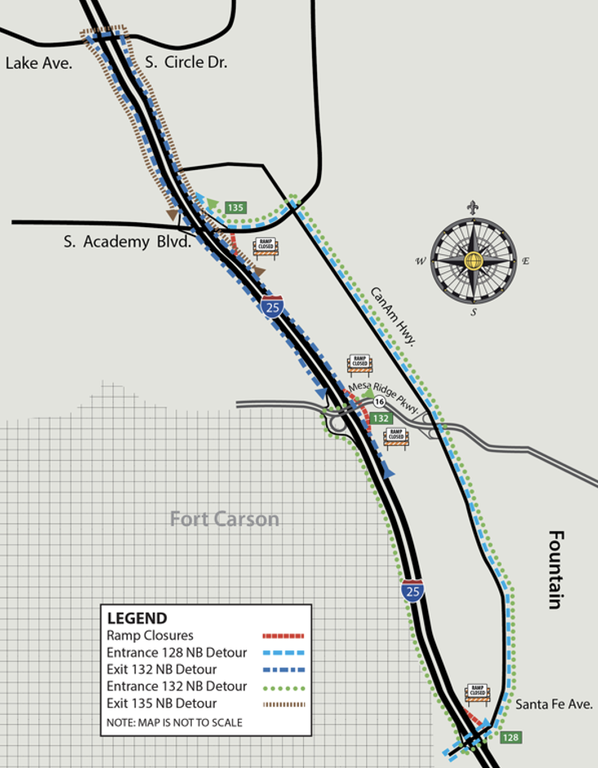
Colorado Springs — Construction on Interstate 25 between South Academy Boulevard and Santa Fe Avenue requires ramp closures on Thursday night and overnight lane closures throughout the week to shift traffic barriers to prepare for the northbound traffic switch from mile 128 to 135.
Beginning at 7 p.m. on Sunday, April 30, and continuing until Wednesday, May 3, drivers can anticipate left lane closures on northbound I-25. On Thursday night May 4, drivers can anticipate various lane closures and ramp closers on northbound I-25 to perform the traffic switch. All lanes reopen at 6 a.m. Monday through Friday, and at 9 a.m. on Saturday.
The traffic switch that was originally scheduled for Saturday night, April 29 has been rescheduled for Thursday night, May 4. Northbound I-25 traffic will move to the newly constructed southbound lanes and will be head-to-head, separated by temporary barrier with 11-foot lanes and two-foot shoulders, so northbound lanes can be constructed. Motorists can expect new on- and off-ramps, lane closures, ramp closures and several detours with the traffic switch.
Northbound I-25 ramp closure detours include:
- Entrance 128 at Santa Fe Avenue.: Traffic will travel north on Santa Fe Avenue / CanAm Highway to South Academy Boulevard., turn west and enter I-25 at Entrance 135.
- Exit 132 at Mesa Ridge Parkway: Traffic will continue north to South Circle Drive, turn around and travel south to Exit 132A or 132B
- Entrance 132 at Mesa Ridge Parkway: Traffic will proceed west to southbound Entrance 132, travel south to Exit 128, turn east onto Santa Fe Avenue, continue north on CanAm Highway to South Academy Boulevard, turn west and enter I-25 at Entrance 135
- Exit 135 at South Academy Boulevard: Traffic will continue north to South Circle Drive, turn around and travel south to Exit 135
Construction schedules are weather-dependent and subject to change
Traffic Impacts
I-25 between U.S. 85/Fountain (mile 127) and South Academy Boulevard (mile 135)
Nighttime closures:
- Sunday, April 30, 7 p.m. to 6 a.m., northbound I-25 left lane closure between Mile Point 127 to 132
- Sunday, April 30, 8 p.m. to 5 a.m., northbound I-25 left…



