WordPress sites being hacked with fake Cloudflare DDoS to distribute malware
 Image courtesy:wordpress.org
Image courtesy:wordpress.org
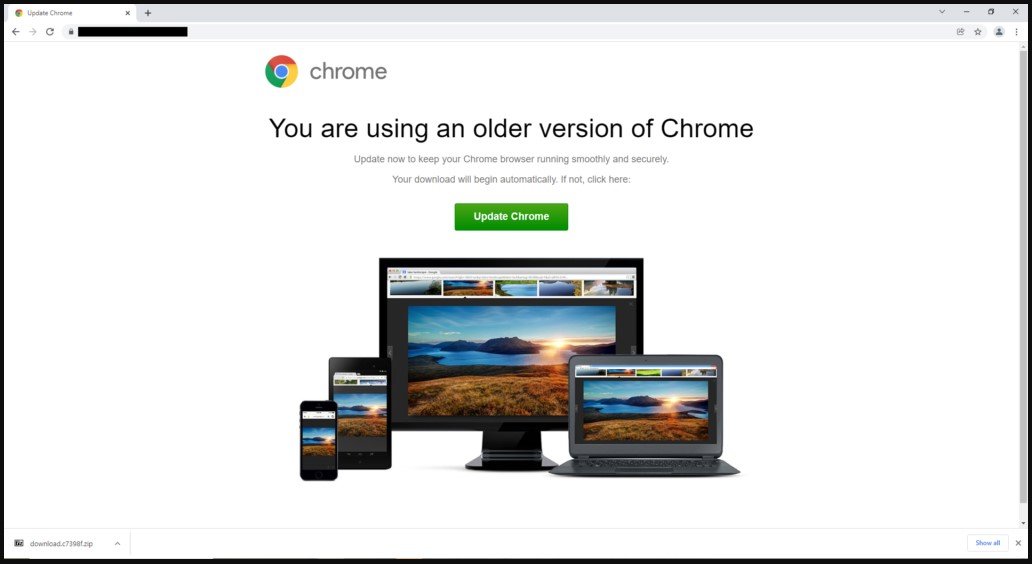
On Saturday, WordPress sites are being hacked for displaying fake Cloudflare DDoS protection pages to circulate malware that installs the NetSupport RAT and the RaccoonStealer password-stealing Trojan.
DDoS protection screens are commonplace on the internet, that protects sites from bots, pinging them with bogus requests which aim to overwhelm them with garbage traffic.
Internet users treat these welcome screens as an unavoidable short-term annoyance that keeps their favorite online resources protected from malicious operatives. Unfortunately, this familiarity serves as an excellent opportunity for malware campaigns, Bleeping Computer reports.
According to the reports by Sucuri, hackers are attacking poorly protected WordPress sites to add a heavily obscure JavaScript payload, displaying a fake Cloudflare protection DDoS screen.
In June 2022, Raccoon Stealer returned to operations when its authors released its second major version and made it available to cybercriminals under a subscription model.
Raccoon 2.0 targets passwords, cookies, auto-fill data, and credit cards saved on web browsers, a wide range of cryptocurrency wallets, and it also has the potential of performing file exfiltration and taking screenshots of the victim’s desktop.