Google Play Protect fails Android security tests once more

Google Play Protect, the Android built-in malware defense system, has failed the real-world tests of antivirus testing lab AV-TEST after detecting just over two thirds out of more than 20,000 malicious apps it was pitted against.
Google’s Android mobile threat protection, which automatically scans over 100 billion apps every day, was introduced during the Google I/O 2017 in May 2017, with rollout to all Android devices starting in July 2017.
Since then, Google Play Protect has been deployed to billions of devices and is now the built-in malware protection on over 2.5 billion active Android devices.
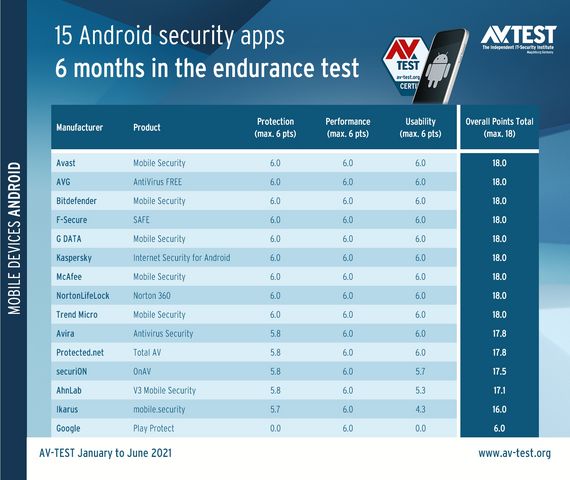
According to AV-TEST’s results, Google’s mobile threat protection solution ranked last out of 15 Android security apps tested over a span of six months, between January to June 2021.
While always running and scanning every app installed and launched on the device, “the endurance test revealed that this service does not provide particularly good security: every other security app offers better protection than Google Play Protect.”
Last of the pack
During this 5-month long endurance test, Google Play Protect detected a little over two-thirds of nearly 20,000 infected apps the testing lab used as part of three rounds of tests.
Each of these testing rounds pitted the security apps against over 3,000 newly-discovered malware samples (up to 24 hours old) and a reference set of more than 3,000 other up to one-month-old samples.
“A total of 5 apps always detected all the attackers 100 percent in the real-time test and in the test with the reference set,” AV-TEST found.
“Finishing in last place, Google Play Protect only detected 68.8 percent in the real-time test and 76.6 percent in the test with the reference set.”
Out of all mobile security apps tested, Bitdefender, G DATA, McAfee, NortonLifeLock, and Trend Micro were the ones that hit a perfect 100% detection rate.
Google Play Protect also mistakenly detected 70 apps as potentially malicious out of almost 10,000 harmless ones installed by AV-TEST from the Play Store and third-party Android app stores.
Given that the Android built-in malware protection solution failed to detect over a third of the 20,000 malware…