Unified API Protection for Telcos and Mobile Carriers – Time to Value
Largest Mobile Carrier Identified 4,600 APIs
in Days, not Weeks, or Months
The security team at the nation’s largest mobile carrier had a problem trying to obtain a consistent and complete inventory of the company’s sprawling API footprint. Business critical API-based applications were driving the mobile carrier’s day-to-day business of managing their mobile network, but the number of APIs were quickly outstripping their ability to keep track of them all.
Key Objectives: A Complete API Catalog
A 2021 security team objective was to obtain a complete running inventory of all their APIs within their organization to ensure that they understood their entire API footprint. Across the organization, they had software groups that supported API application development but worked independently of each other. What resulted was shadow APIs that were not cataloged and were without the oversight of the security team. However, because so many teams were associated with API development, and in the absence of API protection solutions, the cataloging process for both managed and unmanaged APIs was difficult, time-consuming, and lacked accuracy.
Scratching the Surface
When asked how many APIs they had, the security team replied that they had roughly 100 APIs that had been documented manually. They intuitively knew that they were only scratching the surface as there were (likely) hundreds if not thousands of APIs still unaccounted for and not within their existing API catalog.
API Sentinel Automates API Discovery
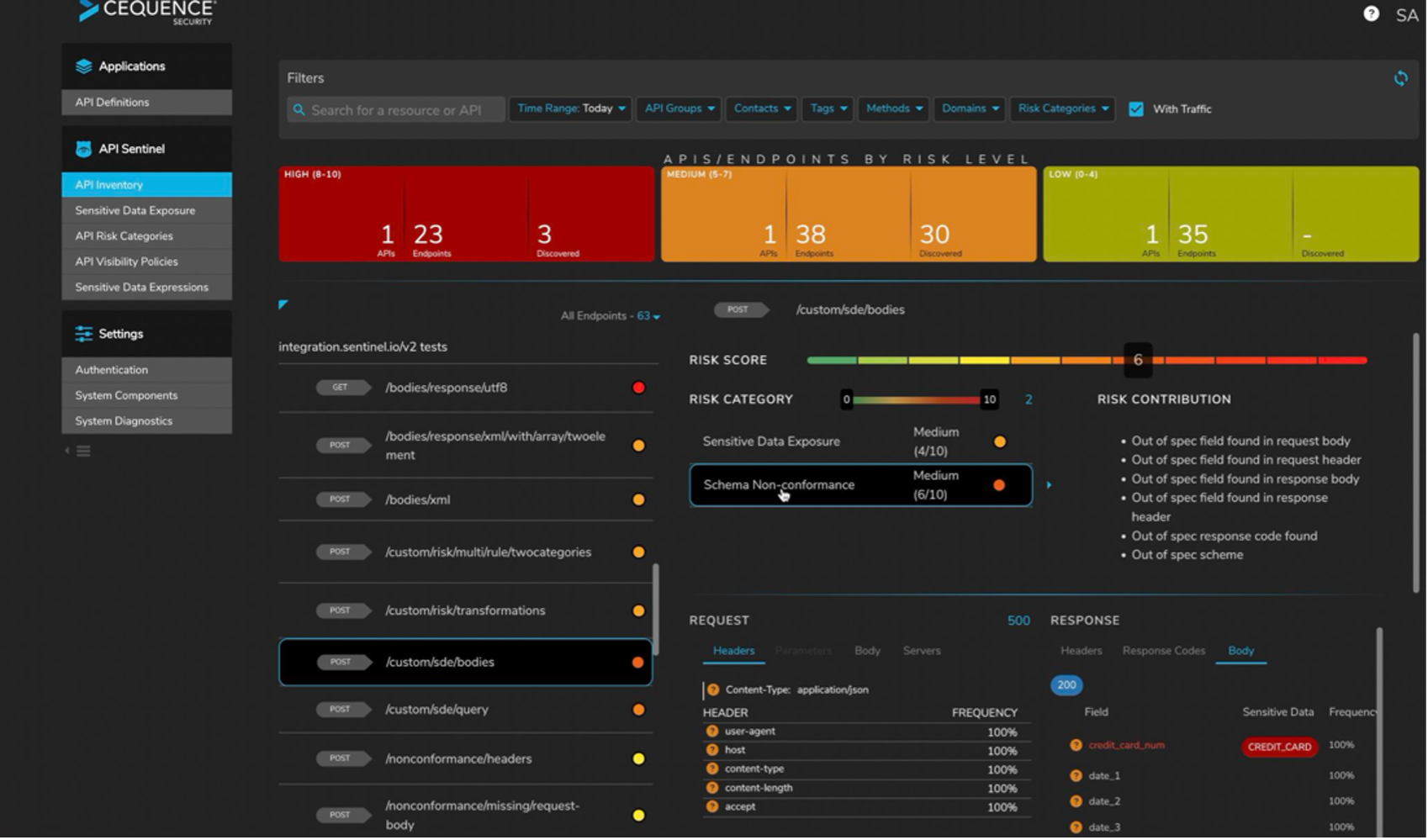
Cequence introduced API Sentinel to the security team and a proof of concept (PoC) was kicked off. By deploying API Sentinel, in just a matter of days, they were able to discover over 4,600 API endpoints that were active across their infrastructure – a 98% increase in API visibility and inventory over what the security team had just days prior to the introduction of Cequence. Moreover, they were able to obtain deep security insights that included the following:
- 6 sensitive data exposure incidents where customer ID, account number and other related business sensitive data was exposed.
- 5 instances of user authentication issues where username and passwords were exposed in cleartext,…