Tag Archive for: API
DarkOwl Ransomware API offers insight into content from ransomware websites hosted on the darknet
/in Internet Security
DarkOwl released Ransomware API, the latest in their suite of darknet products. By enabling users to monitor darknet ransomware sites for their strategic assets – including first and third party vendors – organizations have the most accurate information available as to whether an entity has been extorted or compromised in a ransomware attack.
Ransomware API accesses the same database of darknet content as DarkOwl’s other data products, but targets results to content that was posted on ransomware group websites. These sites include those where actors post about their victims, and frequently leak compromised data that resulted from their attacks. Using this data, a company could expose potential risk for their own organization, assess supply chain vendor risk, or calculate risk to support cybersecurity insurance underwriting processes.
“As ransomware actors become ever more prevalent and advanced in the darknet, companies need tools that allow them to monitor and stay ahead of any cyberattacks. We hope that our deep coverage of this space can help illuminate a criminal economy that is constantly shifting and evolving,” said Mark Turnage, President and CEO of DarkOwl.
DarkOwl’s newest product was developed as a direct result of market demand, and is the first in the industry to offer streamlined, targeted insight into ransomware-hosted content on the darknet. As stated by DarkOwl’s Director of Product Technology, Sarah Prime, “We’re excited to release this new endpoint as a response to what we were hearing from our customers. Our insight into this area of darknet is unique, particularly our historical archive. Through this API product, organization mentions on these sites can now serve as a critical risk indicator.”
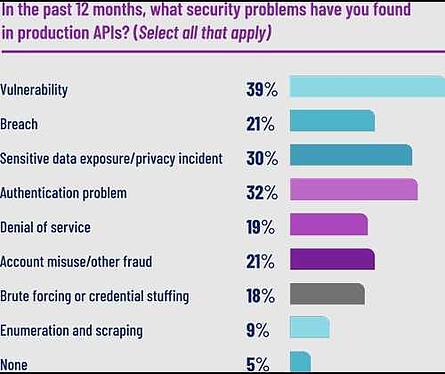
How to Prevent API Abuse
/in Mobile Security

API abuse, when the API is used in an unexpected way, is a growing problem in software development and one of the leading attack vectors cybercriminals exploit. According to a recent security research report that surveyed more than 200 enterprise security professionals, there was a 21.32% growth in malicious API call volume between December 2020 and December 2021. The same study also established that 95% of respondents had suffered an API security incident in the past year.
Source: Salt Security
Examples of API Abuse
Some typical examples of ways that APIs are abused include:
- Man in the Middle attacks: Attackers can use Man in the Middle (MitM) attacks to intercept communications between the app and the backend server. Once communications are intercepted, valuable or sensitive information may be seized and/or manipulated in order to use gain access to backend servers via the API.
- Repackaged or modified apps: Hackers can modify an existing app to include malicious code. The modified app then makes calls to the API to allow the attacker to access sensitive data or to convince genuine users to use the compromised app.
- Scripts or bots: Criminals can use scripts or bots to automate requests to the API in order to scrape data, apply compromised credentials, or overload the system. This is the most common form of API abuse and can lead to denial of service conditions among other conditions which will impact legitimate API users.
- Reverse engineered apps: Attackers can reverse engineer an app to discover the secrets it uses to access its API and the business logic contained within the app. The bad actor can then use this knowledge to make unauthorized calls to the API.
Why is API Abuse a Serious Issue?
Some of the reasons that API abuse is a major threat for organizations include:
- Lack of Awareness: One of the biggest challenges in preventing API abuse is that many organizations are simply unaware that it’s a problem. They may not have experienced an attack yet or may not be monitoring with sufficient granularity to detect this kind of suspicious activity. Specifically, many organizations lack the means to differentiate between a genuine user and a script/bot.
- Mobile Apps…
A Problem Like API Security: How Attackers Hack Authentication
/in Computer Security
There is a sight gag that has been used in a number of movies and TV comedies that involves an apartment building lobby. It shows how people who don’t live there, but who want to get in anyway, such as Girl Guides looking to sell cookies to the tenants – simply run their fingers down every call button on the tenant directory, like a pianist performing a glissando, knowing that at least one of the dozens of apartments being buzzed will let them in simply out of reflex or laziness.
This is a fitting example of broken authentication in the analogue world: an automated system designed to keep non-residents out and to allow them in only by granting individual manual permission that is easily overrun and exploited, without any need for sophisticated tools.
Broken authentication is a term that is used in the world of infosec to describe similar types of outcomes. Organizations of all types that have internet-facing media such as websites and APIs use some form of authentication to prevent the wrong people from “buzzing themselves in,” but these too, are woefully not up to the task.
Attacks that exploit APIs
One of the most common points of weakness is the API attack, in which bad actors force their way in through a variety of techniques, all of which essentially abuse the construction of the APIs own interface, after which they can deposit malware, steal data, or perform other types of crime and sabotage.
One of these techniques is credential stuffing, which involves using stolen usernames and passwords – obtained through data breaches, for example – to fool the API into recognizing a valid ID. This, by the way, is one of many reasons why everyone should change their passwords regularly.
A related technique involves brute (Read more…)




