New Research Confirms Need for End-to-End API Security
Up until just a few years ago, web applications were the dominant platform for all things digital and APIs were tools used to address development corner cases. Driven by mobile device ubiquity, the adoption of the cloud, and the move towards agile, more iterative microservices-based development methodologies, APIs are now the connective tissue for everything we do digitally. The apps we use on our devices for work and pleasure, our favorite shopping, money management, travel web site, and even the cars we drive all use APIs heavily.
Built for machine to machine communications and inclusive of the desired function and payload, developers have come to love APIs for their ability to connect application elements and cloud services together quickly to create engaging user experiences. Attackers, who are developers at heart, love them for the same reasons, but with malicious end goals in mind. To dig into the details behind the explosive use of APIs, the security challenges they represent and how best to address those challenges, Cequence Security recently teamed with ESG to conduct a survey of 366 IT and cybersecurity professionals.
Containers and Cloud Drive API Growth
The survey found that over the next two years, organizations using APIs solely for their web and app development will nearly triple and 41% will use APIs for most of their development, nearly double that of today. Factors driving API usage include the move towards iterative, modular application development methodologies where APIs connect different components to each other. As a proof point, 71% of respondents stated that in two years, at least half of their apps would be microservices based, growing significantly from the current 39%.
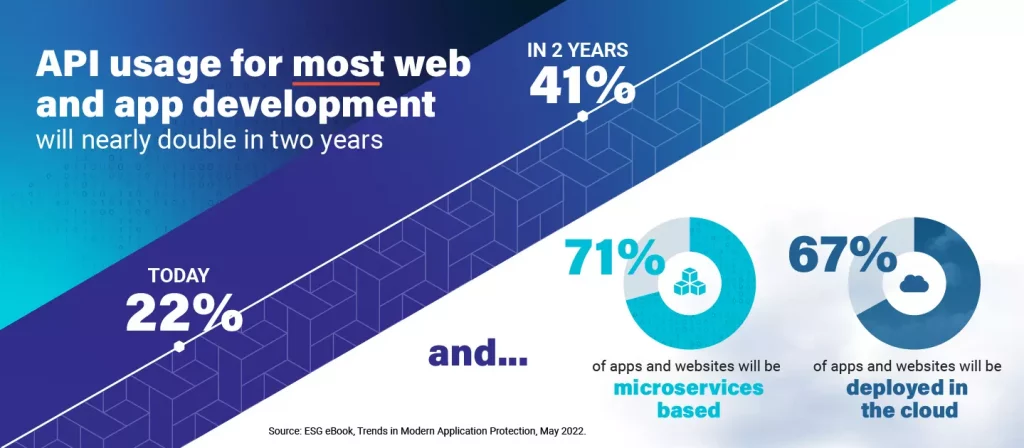
Validating the trend towards deploying the applications where it makes the most sense, cloud vs. datacenter vs. hybrid, 35% of organizations stated that 30% or more of their apps and websites were deployed in the cloud currently, growing to 67% of organizations in two years. In summary, the usage of cloud-native, microservices-based architectures will outpace the growth of cloud-resident applications, meaning many organizations will support hybrid application environments.




