Tag Archive for: spread
Tracking the global spread of malware
/in Computer Security
Approximately 10-16 percent of organizations have shown evidence of malicious command and control (C2) activities, strongly indicating a network breach within the last year, according to Akamai.
![]()
Emotet and QSnatch
Akamai observes nearly seven trillion DNS requests daily and classifies malicious DNS transactions into three main categories: malware, phishing and command and C2. These attacks present a major threat to both enterprises and home users.
They analyzed malicious DNS data and linked attackers to malware such as Emotet, a malware strain that is now one of the most dangerous cybercrime services, and QSnatch, which targets backups or file storage and is the most significant botnet threat in enterprise environments.
According to their data, QSnatch accounted for 36% of infected devices. This malware specifically targets QNAP, a type of NAS device used for backups or file storage by businesses. Although the infection method is still unknown, researchers surmise that QSnatch could infect via exploitation of firmware vulnerabilities or brute force attacks on devices with a default username/password.
Affected devices
Additional findings of the report include:
- 26 percent of affected devices have attempted to reach out to known initial access brokers (IAB) C2 domains, including Emotet-related domains. IABs present a large risk to organizations as their primary role is to initiate the breach and sell access to ransomware groups and other cybercriminal groups.
- Network-attached storage devices are ripe for exploitation as they are less likely to be patched and they hold troves of valuable data. Akamai data shows attackers are abusing these devices through QSnatch.
- Attacks on home networks are seeking to abuse not only traditional devices like computers, but also mobile phones and IoT devices. A significant amount of attack traffic can be correlated with mobile malware and IoT botnets.
“This new report shows the massive range of cybercrime in the modern threat landscape,” said Steve Winterfeld, Advisory CISO at Akamai. “Attackers are unfortunately finding success when they leverage as-a-service hacking tools and are able to combine various tools in a single integrated…
Urgent security warning for Android users over ‘dangerous’ new bug that’s spread across the world
/in Mobile Security
A DANGEROUS malware bug is spreading across the globe and affecting Android users.
The so-called “Xenomorph Android” malware was first spotted last year, but has returned: and can endanger your bank applications.
Now, the bug is back, with worries that it’s spreading quickly without many knowing they have it on their device.
More than 400 baking applications and digital wallets are being targeted by the vicious virus.
Experts at TreatFabric said the malware can automatically hack accounts, including stealing bank account balances.
The bug can also make unauthorised transactions, and transfer money to other accounts without permission.
Xenomorph can now “completely automate the whole fraud chain”, from infecting software to making illicit transactions.
The attacks are concentrated with users in Spain, Turkey and the United States, but experts are worried it could spread.
Android owners have been warned to watch out when downloading any new applications.
Reading reviews and checking the names of developers on applications is a good way to ensure it’s reliable, and not malware.
This comes on the tails of Apple issuing a warning to iPhone users earlier this week.
Users are being urged to utilise the built-in security features on iPhone to protect your data and personal information.
The four part security checkup asks users to begin by setting a strong passcode.
Apple said: “Setting a passcode also turns on data protection, which encrypts your iPhone data with 256-bit AES encryption.”
Using Face ID or Touch ID adds an extra layer of protection, providing a secure and convenient way to unlock your iPhone, authorize payments, and sign in to third-party apps.
Turning on the “Find My” feature is a great help as it can find your device if it’s stolen.
It also allows you to erase your data if you can’t recover your device.
You can also control what features are available without unlocking your iPhone.
Disabling access to certain features can keep your device safer – for example, USB connections.
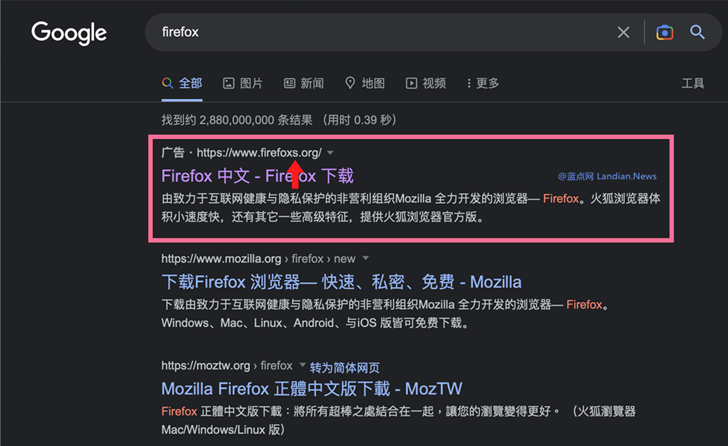
Hackers Using Google Ads to Spread FatalRAT Malware Disguised as Popular Apps
/in Computer Security
Feb 16, 2023Ravie LakshmananAd Fraud / Malware
Chinese-speaking individuals in Southeast and East Asia are the targets of a new rogue Google Ads campaign that delivers remote access trojans such as FatalRAT to compromised machines.
The attacks involve purchasing ad slots to appear in Google search results that direct users searching for popular applications to rogue websites hosting trojanized installers, ESET said in a report published today. The ads have since been taken down.
Some of the spoofed applications include Google Chrome, Mozilla Firefox, Telegram, WhatsApp, LINE, Signal, Skype, Electrum, Sogou Pinyin Method, Youdao, and WPS Office.
“The websites and installers downloaded from them are mostly in Chinese and in some cases falsely offer Chinese language versions of software that is not available in China,” the Slovak cybersecurity firm said, adding it observed the attacks between August 2022 and January 2023.
A majority of the victims are located in Taiwan, China, and Hong Kong, followed by Malaysia, Japan, the Philippines, Thailand, Singapore, Indonesia, and Myanmar.
The most important aspect of the attacks is the creation of lookalike websites with typosquatted domains to propagate the malicious installer, which, in an attempt to keep up the ruse, installs the legitimate software, but also drops a loader that deploys FatalRAT.
In doing so, it grants the attacker complete control of the victimized computer, including executing arbitrary shell commands, running files, harvesting data from web browsers, and capturing keystrokes.
“The attackers have expended some effort regarding the domain names used for their websites, trying to be as similar to the official names as possible,” the researchers said. “The fake websites are, in most cases, identical copies of the legitimate sites.”
The findings arrive less than a year after Trend Micro disclosed a Purple Fox campaign that leveraged tainted software packages Adobe, Google Chrome, Telegram, and WhatsApp as an arrival vector to propagate FatalRAT.
They also arrive amid a broader abuse of Google Ads to serve a wide range of malware, or alternatively, take users to credential phishing pages.
In a related development,…